
ACC140/ACC135 Intro to Financial Accounting_Winter 2024
16. The balance sheet and income statement shown below are for Koski Inc. Note that the firm has no...
The balance sheet and income statement shown below are for Koski Inc. Note that the firm has no amortization charges, it does not lease any assets, none of its debt must be retired during the next 5 years, and the notes payable will be rolled over.
Balance Sheet (Millions of $)
Assets 2014
Cash and securities $ 2,500
Accounts receivable 11,500
Inventories 16,000
Total current assets $30,000
Net plant and equipment $20,000
Total assets $50,000
Liabilities and Equity Accounts payable
$ 9,500
Accruals 5,500
Notes payable 7,000
Total current liabilities $22,000
Long-term bonds $15,000
Total liabilities $37,000
Common stock $ 2,000
Retained earnings 11,000
Total common equity $13,000
Total liabilities and equity $50,000
Income Statement (Millions of $)
2014
Net sales $87,500
Operating costs except depreciation 81,813
Depreciation 1,531
Earnings bef interest and taxes (EBIT) $ 4,156
Less interest 1,375
Earnings before taxes (EBT) $ 2,781
Taxes 973
Net income $ 1,808
Other data:
Shares outstanding (millions)
500.00
Common dividends $632.73
Int rate on notes payable & L-T bonds 6.25%
Federal plus state income tax rate 35%
Year-end stock price $43.39
What is the firm’s current ratio? Current Ratio = Current assets/Current liabilities = 1.36
What is the firm’s quick ratio?
What is the firm’s days sales outstanding? Assume a 365-day year for this calculation. 47.97
What is the firm’s total assets turnover?
What is the firm’s inventory turnover ratio?
What is the firm’s TIE?
What is the firm’s total debt to total capital ratio?
What is the firm’s ROA?
What is the firm’s ROE? ROE = Net income/common equity = 13.91%
What is the firm’s BEP?
What is the firm’s profit margin?
What is the firm’s return on invested capital?
What is the firm’s P/E ratio? 12.0
What is the firm’s book value per share?
What is the firm’s market-to-book ratio?
</pstyle="margin:>
17. Listen to Guillermo and Ana talk about vacation destinations. Indicate whether each statement is...
Listen to Guillermo and Ana talk about vacation destinations. Indicate whether each statement is lógico or ilógico.
1
2
3
4
18. Mary Willis is the advertising manager for Bargain Shoe Store.
Mary Willis is the advertising manager for Bargain Shoe Store. She is currently working on a major promotional campaign. Her ideas include the installation of a new lighting system and increased display space that will add $24,000 in fixed costs to the $270,000 currently spent. In addition, Mary is proposing that a 5% price decrease ($40 to $38) will produce a 20% increase in sales volume (20,000 to 24,000). Variable costs will remain at $24 per pair of shoes. Management is impressed with Mary’s ideas but concerned about the effects that these changes will have on the break-even point and the margin of safety.
Instructions
(a) Compute the current break-even point in units, and compare it to the break-even point in units if Mary’s ideas are used.
(b) Compute the margin of safety ratio for current operations and after Mary’s changes are introduced. (Round to nearest full percent.)
(c) Prepare a CVP income statement for current operations and after Mary’s changes are introduced. (Show column for total amounts only.) Would you make the changes suggested?
Answer:
a) Compute the current break-even point in units, and compare it to the break-even point in units if Svetlana's ideas are used. Current selling price per unit $40 Less: Current variable cost $22 Current contribution margin per unit $18 Current fixed costs $270,000 Break-even point in units = Fixed costs/Contribution margin per unit =$270,000/$18 =15,000 units Proposed selling price per unit $38 Less: Variable cost $22 New contribution margin per unit $16 Proposed fixed costs (270000+34000) $304,000 Break-even point in units = $304,000/$16 =19,000 units The break-even point in units increases from 15,000 to 19,000 if Svetlana's ideas are used. b) Compute the margin of safety ratio for current operations and after Svetlana's changes are introduced. (Round to nearest full percent.) Current operations: Margin of safety = Actual/Budgeted sales - Break-even sales =(20,000 units x $40) - (15,000 units x $40) =$800,000 - $600,000 =$200,000 Margin of safety ratio = Margin of safety (in dollars)/Actual sales =$200,000/$800,000 =25% Proposed by Svetlana: Margin of safety = Actual/Budgeted sales - Break-even sales...
19. Next to the following list of eight characteristics of business
Next to the following list of eight characteristics of business organizations, enter a brief description of how each characteristic applies to general partnerships.
Characteristic Application to General Partnerships
1. Life . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
2. Owners’ liability . . . . . . . . . . . . . . . . . . . . . . . .
3. Legal status . . . . . . . . . . . . . . . . . . . . . . . . . . . .
4. Tax status of income . . . . . . . . . . . . . . . . . . . . .
5. Owners’ authority . . . . . . . . . . . . . . . . . . . . . . .
6. Ease of formation . . . . . . . . . . . . . . . . . . . . . . .
7. Transferability of ownership . . . . . . . . . . . . . . . .
8. Ability to raise large amounts of capital . . . . . . .
20. 4. The Bihar Coal Co. Ltd. has leased of a mine on a royalty of 50 paise per tone of coal raised,...
4.The Bihar Coal Co. Ltd. has leased of a mine on a royalty of 50 paise per tone of coal
raised, with a dead rent of Rs. 30,000 per annum and power to recoup shortworkings
during the first five years of the lease. The output for the first three years was
as follows:
2002 15,000 tonnes; 2003 50,000 tonnes; 2004 75,000 tonnes.
Draw the necessary journal entries in the books of company giving effect to the
above. You are also required to write up the Minimum Rent Account, Royalties Account,
Shortworkings Accout, Landlord Account and Profit and Loss Account.
21. 4.29 A box of nine gloves contains two left-handed gloves and seven right-handed gloves. a. If two..
4.29 A box of nine gloves contains two left-handed gloves and seven right-handed gloves. a. If two gloves are randomly selected from the box, without replacement (the first glove is not returned to the box after it is selected), what is the probability that both gloves selected will be right-handed? b. If two gloves are randomly selected from the box, without replacement (the first glove is not returned to the box after it is selected), what is the probability that there will be one right-handed glove and one left-handed glove selected? c. If three gloves are selected, with replacement (the gloves are returned to the box after they are selected), what is the probability that all three will be left-handed? d. If you were sampling with replacement (the first glove is returned to the box after it is selected), what would be the answers to (a) and (b)?
22. MULTIPLE CHOICE QUESTIONS 39.Which one of the following is not an objective of a system of internal.
MULTIPLE CHOICE QUESTIONS
39.Which one of the following is not an objective of a system of internal controls?
a.Safeguard company assets
b.Overstate liabilities in order to be conservative
c.Enhance the accuracy and reliability of accounting records
d.Reduce the risks of errors
40.Internal controls are concerned with
a.only manual systems of accounting.
b.the extent of government regulations.
c.safeguarding assets.
d.preparing income tax returns.
41.Which of the following is not one of the main factors that contribute to fraudulent activity?
a.Opportunity.
b.Incompatible duties.
c.Financial Pressure.
d.Rationalization.
42.Internal control is defined, in part, as a plan that safeguards
a.all balance sheet accounts.
b.assets.
c.liabilities.
d.capital stock.
43.The most important element of the fraud triangle is
a.financial pressure.
b.incompatible duties.
c.opportunity.
d.rationalization.
44.All of the following requirements about internal controls were enacted under the Sarbanes Oxley Act except
a.independent outside auditors must attest to the level of internal control.
b.companies must develop sound internal controls over financial reporting.
c.companies must continually assess the functionality of internal controls.
d.independent outside auditors must eliminate redundant internal controls.
45.Internal controls are not designed to safeguard assets from
a.natural disasters.
b.employee theft.
c.robbery.
d.unauthorized use.
46.Having one person post entries to accounts receivable subsidiary ledger and a different person post to the Accounts Receivable Control account in the general ledger is an example of
a.inadequate internal control.
b.duplication of effort.
c.external verification.
d.segregation of duties.
47.Having one person responsible for the related activities of ordering merchandise, receiving goods, and paying for them
a.increases the potential for errors and fraud.
b.decreases the potential for errors and fraud.
c.is an example of good internal control.
d.is a good example of safeguarding the company's assets.
48.The custodian of a company asset should
a.have access to the accounting records for that asset.
b.be someone outside the company.
c.not have access to the accounting records for that asset.
d.be an accountant.
23. Static budgets are often used by:
Static budgets are often used by:
A. production departments.
B. administrative departments.
C. responsibility centers.
D. capital projects.
24. (Objective 12-3) Distinguish between general controls and application controls and give two...
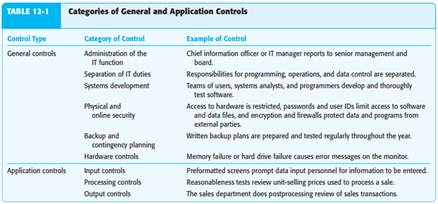
(Objective 12-3) Distinguish between general controls and application controls and give two examples of each.
(Objective 12-3)
INTERNAL CONTROLS SPECIFIC TO INFORMATION TECHNOLOGY
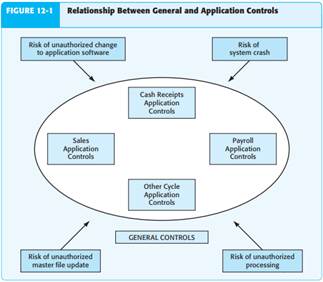
To address many of the risks associated with reliance on IT, organizations often imple - ment specific IT controls. Auditing standards describe two categories of controls for IT systems: general controls and application controls. General controls apply to all aspects of the IT function, including IT administration; separation of IT duties; systems development; physical and online security over access to hardware, software, and related data; backup and contingency planning in the event of unexpected emergencies; and hardware controls. Because general controls often apply on an entity-wide basis, auditors evaluate general controls for the company as a whole. Application controls apply to processing transactions, such as controls over the processing of sales or cash receipts. Auditors must evaluate application controls for every class of transactions or account in which the auditor plans to reduce assessed control risk because IT controls will be different across classes of transactions and accounts. Application controls are likely to be effective only when general controls are effective. Figure 12-1 illustrates the relationship between general controls and application controls. General controls provide assurance that all application controls are effective. Strong general controls reduce the types of risks identified in the boxes outside the general controls oval in Figure 12-1. Table 12-1 describes six categories of general controls and three categories of application controls, with specific examples for each category. Let’s examine these categories of general and application controls in more detail. Similar to the effect that the control environment has on other components of internal control discussed in Chapter 10, the six categories of general controls have an entitywide effect on all IT functions. Auditors typically evaluate general controls early in the audit because of their impact on application controls. Administration of the IT Function The board of directors’ and senior manage - ment’s attitude about IT affect the perceived importance of IT within an organization. Their oversight, resource allocation, and involvement in key IT decisions each signal the importance of IT. In complex environments, management may establish IT steering committees to help monitor the organization’s technology needs. In less complex organizations, the board may rely on regular reporting by a chief information officer (CIO) or other senior IT manager to keep management informed. In contrast, when management assigns technology issues exclusively to lower-level employees or outside
consultants, an implied message is sent that IT is not a high priority. The result is often an understaffed, underfunded, and poorly controlled IT function. Separation of IT Duties To respond to the risk of combining traditional custody, authorization, and record-keeping responsibilities by having the computer perform
those tasks, well-controlled organizations respond by separating key duties within IT. For example there should be separation of IT duties to prevent IT personnel from authorizing and recording transactions to cover the theft of assets. Figure 12-2 shows an ideal separation of duties. Ideally, responsibilities for IT management, systems development, operations, and data control should be separated as follows:
• IT management. The CIO or IT manager should be responsible for oversight of the IT function to ensure that activities are carried out consistent with the IT strategic plan. A security administrator should monitor both physical and online access to hardware, software, and data files and investigate all security breaches.
• Systems development. Systems analysts, who are responsible for the overall design of each application system, coordinate the development and changes to IT systems by IT personnel responsible for programming the application and personnel outside IT who will be the primary system users (such as accounts receivable personnel). Programmers develop flowcharts for each new applica - tion, prepare computer instructions, test the programs, and document the results. Programmers should not have access to input data or computer operations to avoid using their knowledge of the system for personal benefit. They should be allowed to work only with test copies of programs and data so they can only make software changes after proper authorization.
• Operations. Computer operators are responsible for the day-to-day operations of the computer following the schedule established by the CIO. They also monitor computer consoles for messages about computer efficiency and malfunctions. A librarian is responsible for controlling the use of computer programs, trans - action files, and other computer records and documentation. The librarian releases them to operators only when authorized. For example, programs and transaction files are released to operators only when a job is scheduled to be pro - cessed. Similarly, the librarian releases a test copy to programmers only on approval by senior manage ment. Network administrators also affect IT operations as they are responsible for planning, implementing, and maintaining operations of the network of servers that link users to various applications and data files.
• Data control. Data input/output control personnel independently verify the quality of input and the reasonableness of output. For organizations that use databases to store information shared by accounting and other functions, database adminis - trators are responsible for the operation and access security of shared databases.
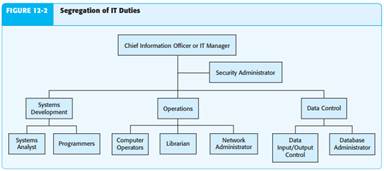
Naturally, the extent of separation of duties depends on the organization’s size and complexity. In many small companies, it is not practical to segregate the duties to the extent illustrated in Figure 12-2. Systems Development Systems development includes:
• Purchasing software or developing in-house software that meets the organiza - tion’s needs. A key to implementing the right software is to involve a team of both IT and non-IT personnel, including key users of the software and internal auditors. This combination increases the likelihood that information needs as well as software design and implementation concerns are properly addressed. Involving users also results in better acceptance by key users.
• Testing all software to ensure that the new software is compatible with existing hardware and software and determine whether the hardware and software can handle the needed volume of transactions. Whether software is purchased or developed internally, extensive testing of all software with realistic data is critical. Companies typically use one or a combination of the following two test approaches:
1. Pilot testing: A new system is implemented in one part of the organization while other locations continue to rely on the old system.
2. Parallel testing: The old and new systems operate simultaneously in all locations. Proper documentation of the system is required for all new and modified software. After the software has been successfully tested and documented, it is transferred to the librarian in a controlled manner to ensure only authorized software are ultimately accepted as the authorized version. Physical and Online Security Physical controls over computers and restrictions to on - line software and related data files decrease the risk of unauthorized changes to programs and improper use of programs and data files. Security plans should be in writing and monitored. Security controls include both physical controls and online access controls.
• Physical controls. Proper physical controls over computer equipment restrict access to hardware, software, and backup data files on magnetic tapes or disks, hard drives, CDs, and external disks. Common examples to physically restrict unauthorized use include keypad entrances, badge-entry systems, security cameras, and security personnel. More sophisticated controls only allow physical and online access after employee fingerprints are read or employee retinas are scanned and matched with an approved database. Other physical controls include monitoring of cooling and humidity to ensure that the equipment functions properly and installing fire-extinguishing equipment to reduce fire damage.
• Online access controls. Proper user IDs and passwords control access to software and related data files, reducing the likelihood that unauthorized changes are made to software applications and data files. Separate add-on security software packages, such as firewall and encryption programs, can be installed to improve a system’s security. (See page 388 for a description of firewall and encryption programs.) Backup and Contingency Planning Power failures, fire, excessive heat or humidity, water damage, or even sabotage can have serious consequences to businesses using IT. To prevent data loss during power outages, many companies rely on battery backups or on-site generators. For more serious disasters, organizations need detailed backup and contingency plans such as off-site storage of critical software and data files or out - sourcing to firms that specialize in secure data storage. Backup and contingency plans should also identify alternative hardware that can be used to process company data. Companies with small IT systems can purchase replacement computers in an emergency and reprocess their accounting records by using backup copies of software and data files. Larger companies often contract with IT data centers that specialize in providing access to off-site computers and data storage and other IT services for use in the event of an IT disaster.
25. Jem Clothes, Inc., is a 25-store chain concentrated in the northeastern United States that sells...
Internal Controls
Jem Clothes, Inc., is a 25-store chain concentrated in the northeastern United States that sells ready-to-wear clothes for young men and women. Each store has a fulltime manager and an assistant manager, both of whom are paid a salary. The cashiers and sales personnel are typically young people working part-time who are paid an hourly wage plus a commission based on sales volume. The accompanying flowchart for Problem 5 depicts the flow of a sales transaction through the organization of a typical store. The company uses unsophisticated cash registers with four-part sales invoices to record each transaction. These sales invoices are used regardless of the payment type (cash, check, or bank card). On the sales floor, the salesperson manually records his or her employee number and the transaction (clothes, class, description, quantity, and unit price), totals the sales invoice, calculates the discount when appropriate, calculates the sales tax, and prepares the grand total. The salesperson then gives the sales invoice to the cashier, retaining one copy in the sales book. The cashier reviews the invoice and inputs the sale. The cash register mechanically validates the invoice, automatically assigning a consecutive number to the transaction. The cashier is also responsible for getting credit approval on charge sales and approving sales paid by check. The cashier gives one copy of the invoice to the customer and retains the second copy as a store copy and the third for a bank card, if a deposit is needed. Returns are handled in exactly the reverse manner, with the cashier issuing a return slip. At the end of each day, the cashier sequentially orders the sales invoices and takes cash register totals for cash, bank card, and check sales, and cash and bank card returns. These totals are reconciled by the assistant manager to the cash register tapes, the total of the consecutively numbered sales invoices, and the return slips. The assistant manager prepares a daily reconciliation report for the store manager’s review. The manager reviews cash, check, and bank card sales and then prepares the daily bank deposit (bank card sales invoices are included in the deposit). The manager makes the deposit at the bank and files the validated deposit slip. The cash register tapes, sales invoices, and return slips are forwarded daily to the central data processing department at corporate headquarters for processing. The data processing department returns a weekly sales and commission activity report to the manager for review.
Required
a. Identify six strengths in the Jem Clothes system for controlling sales transactions.
b. For each strength identified, explain what problem(s) Jem Clothes has avoided by incorporating the strength in the system for controlling sales transactions.
Use the following format in preparing your answer.
1. Strength
2. Problem(s) Avoided